Forensic Data Recovery from Smart Locks and Access Control Systems: Retrieving Event Logs from Minimal Embedded Storage
Introduction
Smart locks, key card readers, and centralized access control systems are the silent gatekeepers of modern properties—from corporate offices and data centers to hospitality venues and multi-family homes. These devices record every entry and denial, creating an irrefutable chronological record of who accessed a space, when, and how.
This access event log becomes critical evidence in legal, security, or civil disputes—whether investigating a hotel room breach, confirming employee compliance, or verifying insurance claims after a break-in.
However, the hardware itself is designed for low power consumption and physical resilience, not easy data access. When a smart lock fails—due to physical tampering, battery depletion leading to data corruption, or liquid damage—the event log is often trapped within tiny, proprietary embedded memory chips.
Retrieving this data requires specialized embedded systems forensics, where recovery experts use highly invasive techniques like JTAG/UART and Chip-Off to bypass the failed system and extract the minimal, non-standard memory chip holding the critical log history.
The Access Control Recovery Challenge: Non-Standard Storage
Smart locks and access control units present unique challenges that are distinct from recovering data from traditional computers or mobile devices.
1. Minimal and Highly Integrated Storage
Access control systems prioritize security and power efficiency. They do not use large, standardized SSDs or HDDs.
-
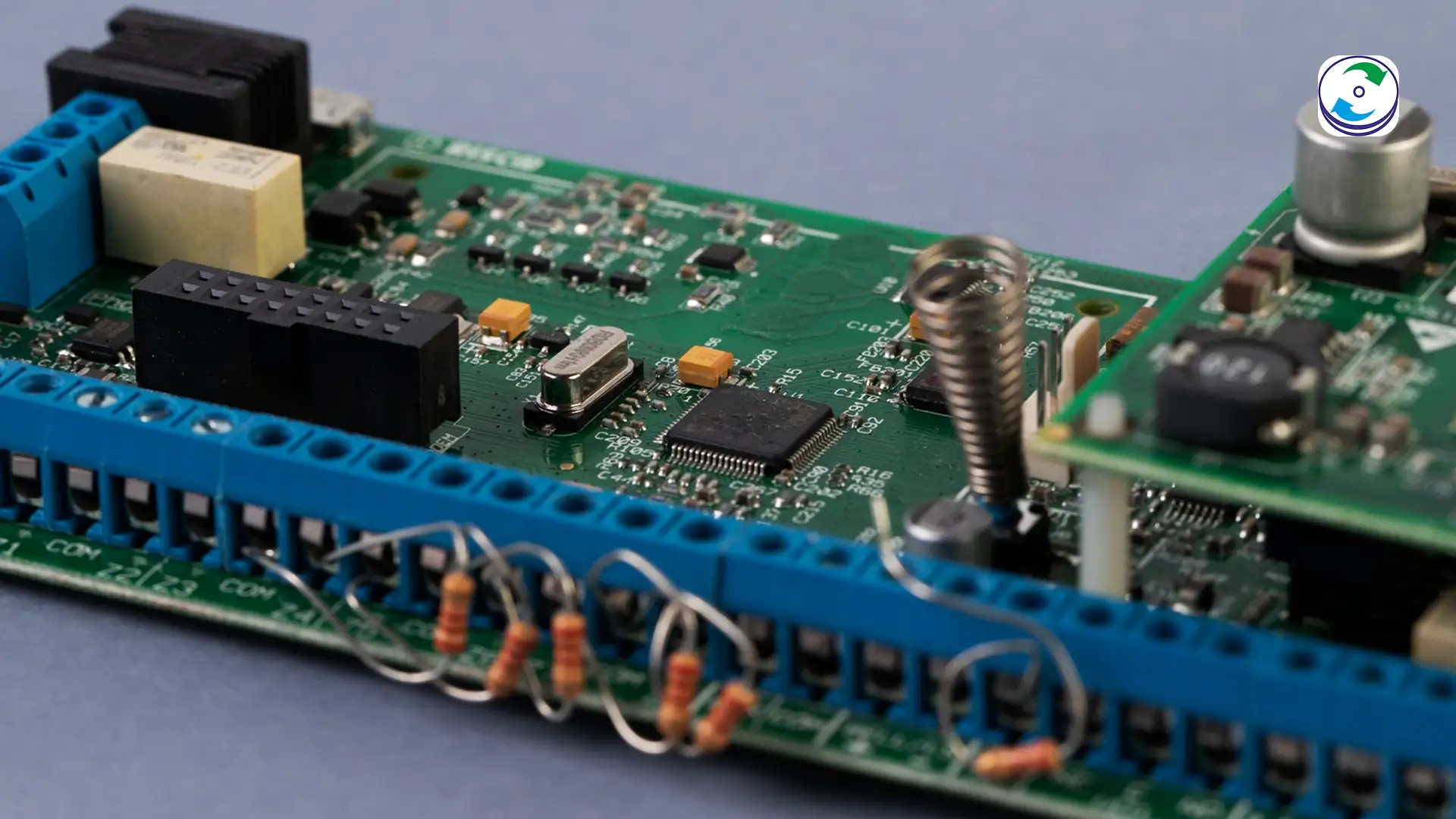
SPI Flash and Secure eMMC: The critical event logs, user credentials, and configuration settings are typically stored on tiny SPI (Serial Peripheral Interface) Flash or small, secure eMMC chips. These components are surface-mounted directly onto the small circuit board inside the lock unit or reader, making them extremely difficult to access without specialized equipment.
-
Encrypted Log Structures: Many commercial and enterprise-grade locks employ internal encryption methods that bind the log data to the device’s unique hardware ID or a secure boot process. If the main processor fails, the raw data extracted from the memory chip will be cryptographically locked without the necessary decryption key.
2. Battery Failure and Log Corruption
Battery power is essential for data integrity in most smart locks, as they typically use volatile memory for temporary log buffering.
-
Sudden Power Loss: A complete and sudden battery depletion or a power surge can corrupt the last few critical entries or damage the index structure of the event log file system. This often results in a partially recoverable log that is missing the most relevant, recent entries detailing the access attempts immediately preceding the failure.
-
Proprietary File Systems: The log data is stored in a proprietary format optimized for minimal resource usage, not a standard operating system file structure. Forensic analysis must first reverse-engineer the lock’s log structure to correctly interpret the raw binary data.
The Forensic Protocol: Accessing the Embedded Memory
When a smart lock is damaged, the forensic priority is to establish a direct electrical connection to the memory chip, bypassing the corrupted or failed main system controller.
Method 1: JTAG/UART Access (Non-Destructive)
This method is used when the device is physically intact but fails to power on or communicate normally.
-
Locating Test Points: The forensic specialist must locate and identify the minuscule JTAG (Joint Test Action Group) or UART (Universal Asynchronous Receiver-Transmitter) test points on the circuit board. These are the low-level communication channels used during the lock’s manufacturing and debugging process.
-
Micro-Soldering Connection: Ultra-fine probes or micro-soldering wires are attached to these points. This requires high-magnification optics and a steady hand to avoid bridging the tiny contacts.
-
Command Injection: Via the JTAG or UART port, the specialist can communicate directly with the lock’s core microcontroller. They can then issue specific, low-level commands to force the controller to dump the contents of the SPI Flash or eMMC memory to an external forensic workstation. This is considered the least invasive method to acquire data.
Method 2: In-Circuit Programming (ICP)
If the main controller is completely dead but the memory chip itself is intact, ICP is used to target the memory directly.
-
Direct Chip Connection: A specialized programming clip is physically attached to the legs or pads of the memory chip while it remains soldered to the PCB.
-
External Read: An external programmer is used to provide power and communication signals directly to the memory chip, effectively isolating it from the rest of the failed circuit. This allows for a bit-for-bit raw image acquisition of the chip’s contents, capturing the complete, scrambled log data.
Method 3: Chip-Off Forensics (Physical Destruction)
In cases where the smart lock or reader is severely damaged (e.g., shattered, water-logged, or burned), the memory chip must be physically removed.
-
Surgical Removal: Using a BGA rework station, the tiny SPI Flash or eMMC chip is surgically de-soldered from the logic board.
-
Raw Data Extraction: The extracted chip is mounted in a custom adapter (often required due to non-standard chip dimensions) and a raw binary image of the data is created.
-
Log Reconstruction: The raw binary data is then analyzed by specialized software. This phase involves:
-
Decrypting the event logs using proprietary algorithms.
-
Defragmenting and reconstructing the log entries.
-
Timestamp Correction (critical due to battery-induced clock drift) to establish an accurate “who and when” timeline.
-
Conclusion: The Irrefutable Access Timeline
The data trapped inside a failed smart lock or access control system often provides the only unbiased account of events—who entered a room, which credential was used, and at what precise moment. This information can be pivotal in legal discovery, security audits, and establishing liability.
Relying on cloud backups is often insufficient, as many local failures, such as a battery depletion or physical tampering, occur before the last successful cloud sync. The only way to retrieve the final, critical logs is through direct access to the device’s minimal embedded memory.
If your organization is dealing with a failure in a security or access system, do not attempt to reset or power cycle the device. Contact DataCare Labs immediately to utilize our expertise in JTAG/UART forensic acquisition and Chip-Off data recovery, ensuring the irrefutable access timeline is preserved and retrieved.